According to SNS insiders, the global market size was USD 10.68 billion in 2021 and is expected to reach USD 18.18 billion by 2028. The Asia Pacific region will hold the largest market share among other region due to high need.
- One of the central tenets of network
security is that reducing the number and complexity of services
offered reduces the opportunity for attackers to break in. - A
number of systems send RST responses to the probes regardless of
whether the port is open or not. - This is dominated by the absorption of light by water (the primary component in the eye) at different wavelengths.
- A Very Small Aperture Terminal (VSAT) is a two-way satellite ground station with a small dish antenna, typically measuring between and meters in diameter.
Parental control may not be able to completely block some APPs and web pages. The challenge of web filtering is compounded by the changing nature of the way employees interact with web resources. Increasingly, users are connecting to the corporate web from home, on the road and from other locations on a variety of devices that are unprotected by firewalls and other perimeter defenses. There are also buttons for testing internet speed, checking for obstructions, adjusting network settings, and looking at network statistics. The courts in some countries or jurisdictions will not apply California law to some types of disputes. If you are resident in one of those countries or jurisdictions, then where California law is excluded from applying, your country’s laws will apply to such disputes which are related to this Agreement.
Account setup
A successful Ping request and the response would show that the System in a network to be a “Live Host”. If you want to check out 192.168.7.1 your target system then it will be your first step to getting the basic information that the target machine is alive or dead. When compiled with OpenSSL support or distributed as source code, Insecure.Com LLC believes that Nmap falls under U.S. We distribute Nmap under the TSU exception for publicly available encryption software defined in
m[blue]EAR 740.13(e)m[][33]. Source is provided to this software because we believe users have a right to know exactly what a program is going to do before they run it.
While it can be used maliciously, like many networking tools, its design and primary function serve network security and analysis. Its use rapidly increased in 2001 along with an increase in computer worms, which scan for new hosts in order to automatically spread. An example worm during that time was the Code Red worm, which would scan for open TCP port 80 then leverage a common vulnerability to spread to new hosts. The above process of sending ICMP request is also called ping scan, which is provided by the operating system’s ping command. Of the 36 known scans in our dataset, the tri-algorithm approach detected 34 of them. The overall detection rate for the tri-algorithm approach was then 94.44%. This compares to individual detection rates of just 50.00% for in-degree, 52.78% for TRW, and 8.33% for rate-limiting.
Platform Segment Analysis
Thus, light is not only emitted from the top surface of the chip but also from the sides. Light that strikes the LED chip surface at an angle greater than the critical angle of the dielectric interface is internally reflected.
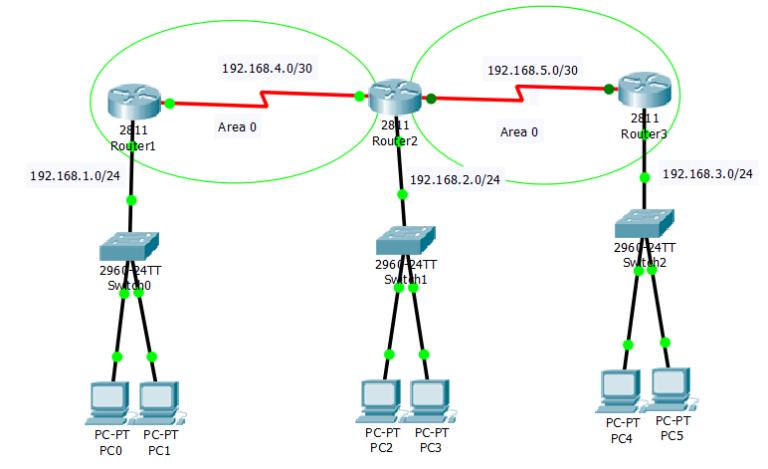
Proposed Architecture
According to the literature, the size range of aerosol particles to be only from 0.1 to 1 μm another authors indicate that the size of aerosol is between 0.01 and 10 μm in radius. Another definition of aerosol is extremely-fine liquid droplets or solid particles that remain suspended in air as fog or smoke. Beam dispersion, atmospheric absorption, rain, fog, snow, interference from background light sources (including the sun), shadowing, pointing stability in wind, and pollution. FSO technology is often used in various applications, including point-to-point communication between buildings, last-mile connectivity, and disaster recovery scenarios where traditional wired or wireless connections are unavailable. It offers a unique and valuable solution for specific use cases where high-speed, secure, and license-free communication is essential. Communication between transmitter and receiver racks can be facilitated by configuring a cylindrically shaped cluster with the racks placed on the cluster’s border. An alternative approach to eliminate the line-of-sight requirement is to install mirrors on the ceilings of the datacenter to facilitate further interconnect options.
